Configuring NGINX as a Reverse Proxy server on a Synology NAS server

200514
As you might already be aware, the Nginx server is coming pre-installed with your Synology NAS server. You can obtain some fundamental information about it [here].
One of the abilities of the Nginx server is that it can be configured as a reverse proxy server to other hosts. That means, it can handle domain requests reaching a specific host and then redirects them to other hosts (e.g., to other machines in your network) according to the specific domain which is served by the appropriate host.
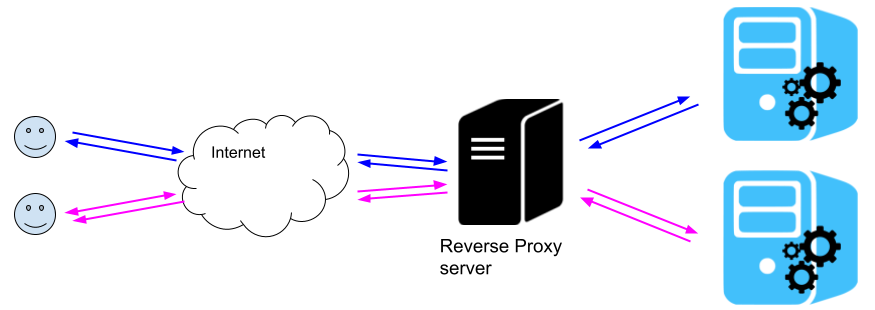
This is quite useful when you have only 1 internet broadband connection to your ISP and you want to maintain multiple domains located in various machines of your local (inner) network. Then, defining a reverse proxy server is a good and cheap solution if you want those domains to be accessible also from the outside world, i.e., from the web.
Thus, if for instance, we have configured our ISP’s router to forward ports 80 and 443 to our Synology NAS server, then we can configure NAS’ Nginx instance as a reverse proxy server.
Setting up a reverse proxy using the Synology DSM GUI
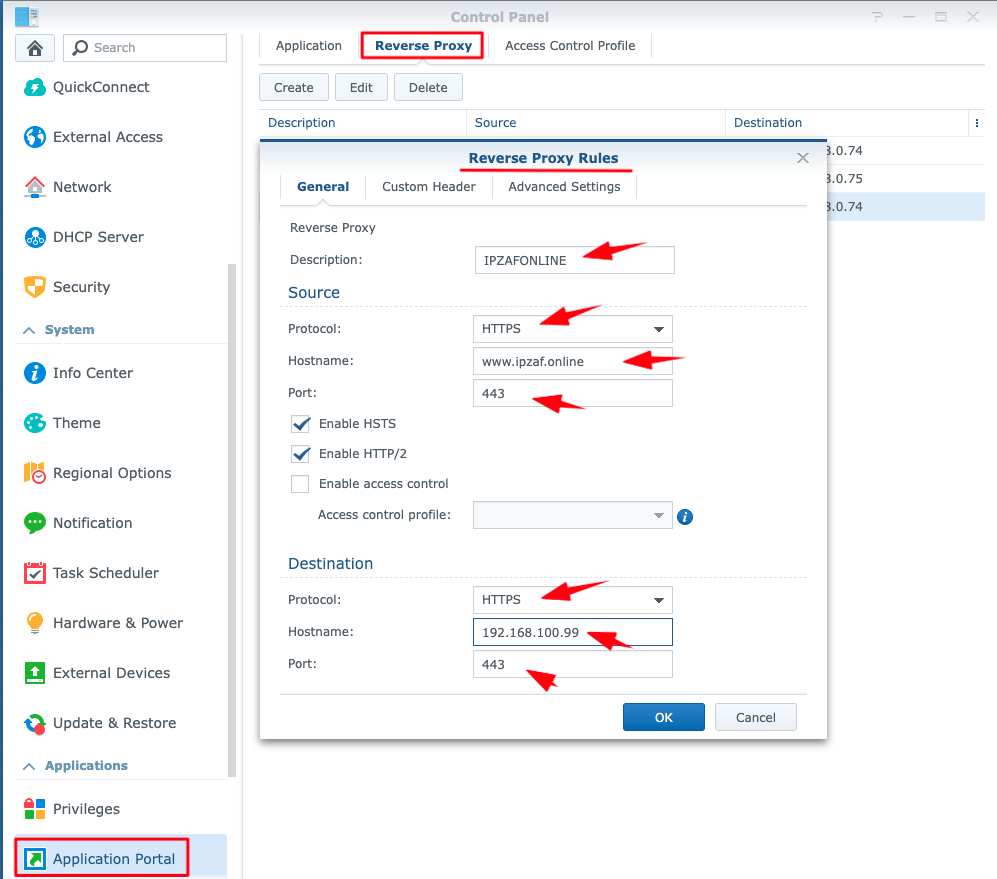
Setting up Nginx to be a reverse proxy server for a particular host is enough simple. The reverse proxy server should be a Synology NAS server accepting the standard http/https request from the internet via appropriate settings (redirection) of our ISPs broadband router. For this purpose, we have to use the Application Portal in the Control Panel of this NAS server. Then we can define our proxy by setting up the Reverse Proxy Rules, in Reverse Proxy Tab.
Below are the settings for setting up a host domain named www.ipzaf.onilne, using the secure HTTPS protocol and listening in the standard 443 port in an internal/local IP 192.168.100.99
(Note that all references here are for DSM 6.2 version).
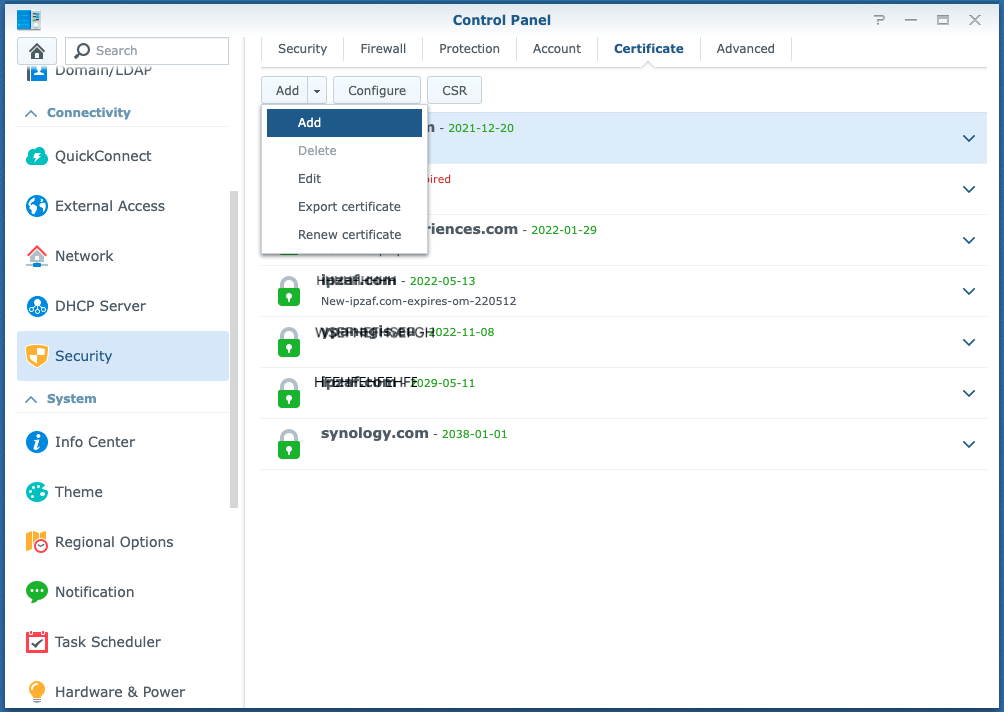
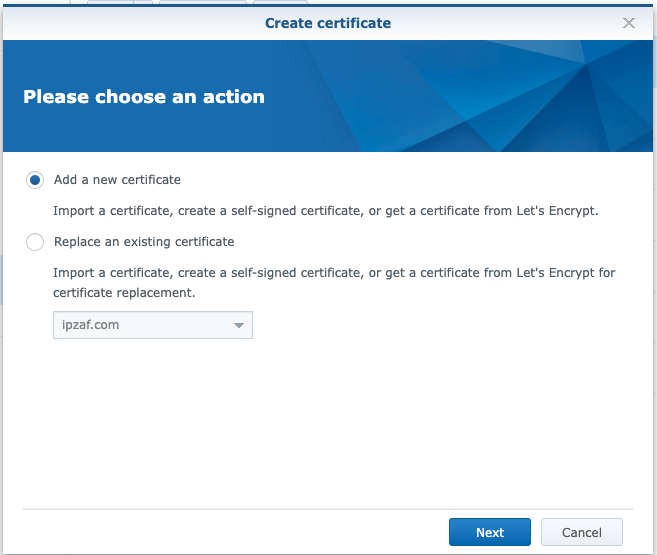
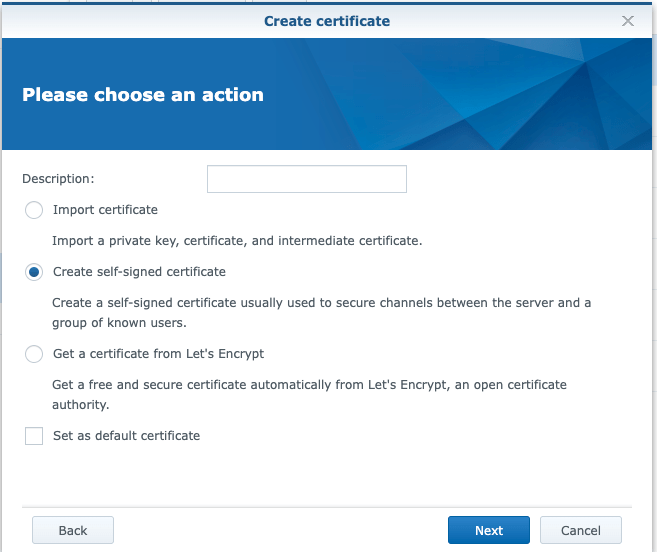
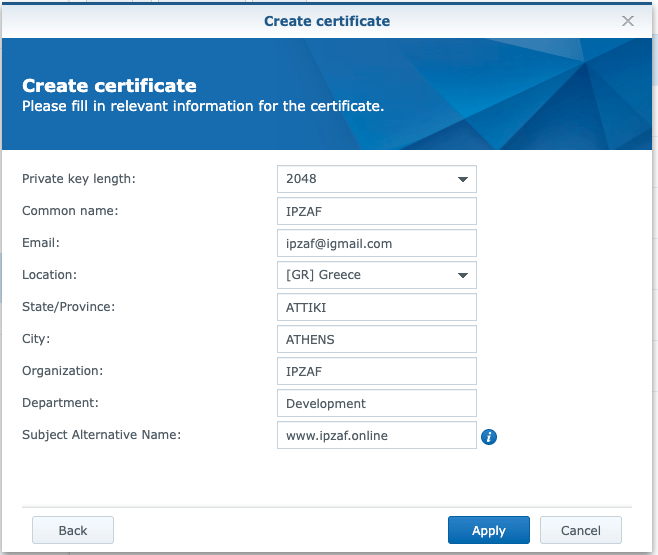
As a next step, we can assign an SSL Certificate to the Hostname we defined above. So, in the Synology NAS server acting as a reverse proxy server, we can use any self-signed (or a CA obtained) Certificate and then configure (assign) it to the domain/host www.ipzaf.online. Follow the steps below (Control Panel –> Security –> Certificate … Configure for a self-signed Certificate):

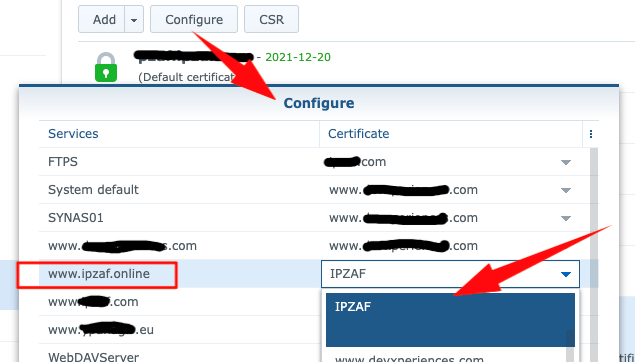
Where Reverse Proxy settings are stored
Setting up a reverse proxy via DSM GUI, as we have seen above, results in a new server block to automatically be generated and added to the server.ReverseProxy.conf NGINX configuration file inside the folder /etc/nginx/app.d. Below you can see it (which also includes the SSL certificate assigned to it):
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name www.ipzaf.online;
ssl_certificate /usr/syno/etc/certificate/ReverseProxy/bd520669-5007-3164-bf16-bf02fa5aedf7/fullchain.pem;
ssl_certificate_key /usr/syno/etc/certificate/ReverseProxy/bd520669-5007-3164-bf16-bf02fa5aedf7/privkey.pem;
add_header Strict-Transport-Security "max-age=15768000; includeSubdomains; preload" always;
location / {
proxy_connect_timeout 60;
proxy_read_timeout 60;
proxy_send_timeout 60;
proxy_intercept_errors off;
proxy_http_version 1.1;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass https://192.168.100.99:443;
}
error_page 403 404 500 502 503 504 @error_page;
location @error_page {
root /usr/syno/share/nginx;
rewrite (.*) /error.html break;
allow all;
}
}
Setting a Virtual host server in another Synology NAS Server
The host listening in this IP (192.168.100.99) can be any kind of host in our internal (local) LAN. In case this is another Synology NAS server, we can use it to define in it a new Virtual Host for the www.ipzaf.online. We can do that in Web Station –> Virtual Host –> Create. Below you can see the settings for a WordPress/Apache/PHP site.
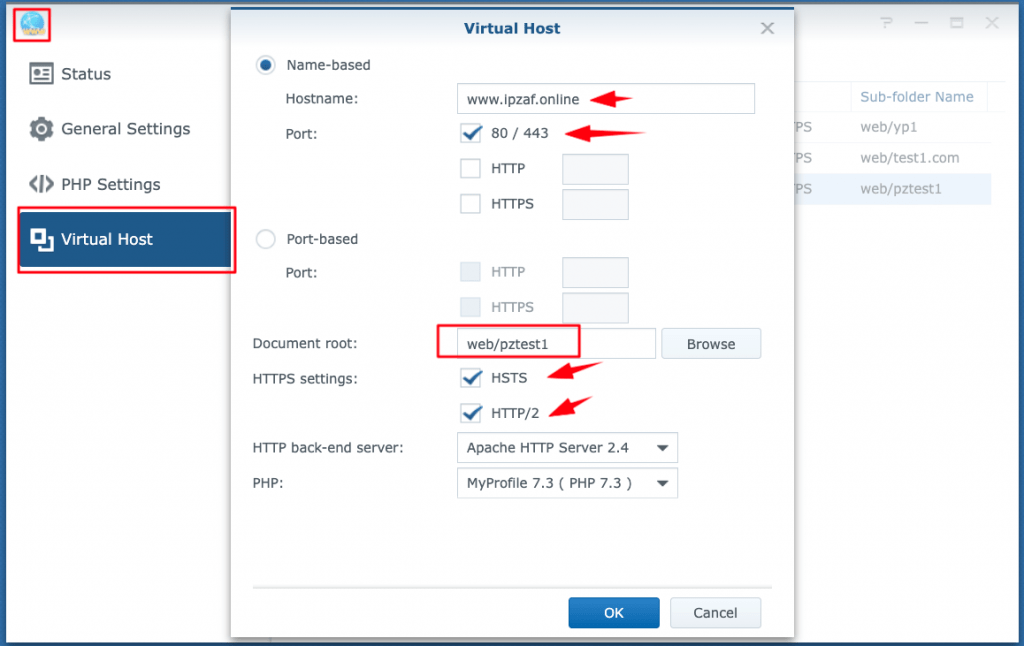
Where Virtual host settings are stored
After we have set it up, a new host block is automatically generated and added to the httpd-vhost.conf Apache configuration file inside the folder /usr/local/etc/apache24/sites-enabled. Below you can see it:
<VirtualHost *:80 *:443>
ServerName www.ipzaf.online
SetEnv HOST www.ipzaf.online
DocumentRoot "/volume3/web/pztest1"
<IfModule dir_module>
DirectoryIndex index.html index.htm index.cgi index.php index.php5
</IfModule>
<Directory "/volume3/web/pztest1">
Options MultiViews FollowSymLinks ExecCGI
AllowOverride All
<IfModule authz_core_module>
Require all granted
</IfModule>
</Directory>
<FilesMatch "\.(php[345]?|phtml)$">
SetHandler "proxy:unix:/run/php-fpm/php-caae0ba2-8365-462f-a019-e88c88a9cc9d.sock|fcgi://localhost"
</FilesMatch>
</VirtualHost>
Setting up a reverse proxy manually
This is a NOT recommended option, for nonexperienced users, so use it at your own risk. We cat follow this approach in cases where there are some necessary customizations (e.g. some special directives/blocks, etc) that are not covered by default using the GUI way. This approach requires a host’s block in an NGINX configuration file. you should do that by adding it inside the /usr/local/etc/nginx/sites-enabled folder (which is a symlink of the sites-enabled folder).sites-enabled -> /usr/local/etc/nginx/sites-enabled
The ‘real’ folder /usr/local/etc/nginx/sites-enabled accepts any file name, so you can add a custom configuration file there and name it as you wish. For example, you can create the file MyCustomCode.conf inside it.
In this file, we can configure an appropriate host block for any host/domain inside our local (internal) network. Let’s say that we have set up a domain ‘www.mydomain2.com’ (e.g. for a WordPress site) on our host with IP 192.168.100.99. If a client from the internet requests www.mydomain2.com in his/her browser, then he/she will be redirected to the internal host 192.168.100.99.
You can see bellow the host block that says to Nginx to act as a reverse proxy server:
user01@nas01: $ cat /usr/local/etc/nginx/sites-enabled/MyCustomCode.conf
# Reverse Proxy block configuration for the internal host web server listening to domain 'www.ipzaf.online'
# That means that if a client from the internet types www.mydomain2.com he/she will be redirected to the internal host: 192.168.100.99.
# The block also redirects HTTP to HTTPS, using the error page with 497 code.
server {
listen 80; ## listen for ipv4; this line is default and implied
#listen [::]:80; ## listen for ipv6
listen 443 ssl;
#listen [::]:443 ssl;
error_page 497 https://$host:$server_port$request_uri;
server_name www.ipzaf.online;
#return 301 https://$host$request_uri;
location / {
proxy_connect_timeout 60;
proxy_read_timeout 60;
proxy_send_timeout 60;
proxy_intercept_errors off;
proxy_http_version 1.1;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass https://192.168.100.99:443/;
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503 http_504;
proxy_redirect https://192.168.100.99:443/ https://$host:$server_port/;
proxy_buffering off;
}
}
user01@nas01: $
NB: The above example block also redirects HTTP to HTTPS, using the error page with 497 code.
In the case that the internal host with IP 192.168.100.99 is an Apache server, then that server’s Apache configuration should have been set up with a Virtual Host with domain www.mydomain2.com and listening to port 443 (HTTPS), as we have seen above. (You can also see [here] how you can do that).
That’s it!
Thank you for reading!