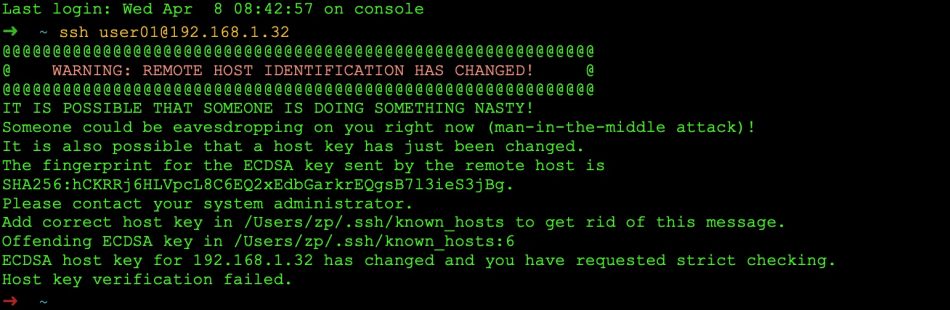
SSH – WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED!
201416
This is a common warning message of the Secure Shell (ssh). In most cases, it shows that the ssh server configuration you are trying to connect to has somehow been changed.
In a local network, this often happens after a change of an SSL certificate and/or a component update at your remote machine (in this case this is a Synology NAS server).
NB: You should have been warned like that because this can also be an alarm for a malicious situation, where someone between your machine and the remote host, tries to convince you that this is the remote host. This is known as the ‘man-in-the-middle attack‘ but we are not going into detail with it.
In such a case, you probably have to update your ~/.ssh/known_hosts file.
Obtain the rsa key from remote hist and update the local known.hosts file
First, using a Terminal window in your local machine, check the server’s existing key in your ~/.ssh/known_hosts file:
$ ssh-keygen -F 192.168.1.32 -l
➜ ~ ssh-keygen -F 192.168.1.32 -l # Host 192.168.1.32 found: line 4 192.168.1.32 ECDSA SHA256:rAd7OhJUIgV4XjdEHkYLtn3T4ITgOQ+wvF4KzEDVAlE ➜ ~
Get the RSA key of your server:
$ ssh-keyscan -t rsa 192.168.1.32
➜ ~ ssh-keyscan -t rsa 192.168.1.32 # 192.168.1.32:22 SSH-2.0-OpenSSH_7.4 192.168.1.32 ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCe2PBBtm0GzJMyXTssrzGU21p9IUbU0QOCWbMCGoEUbP2Qu0HWvmj2IOxrpcNdGaMVRlbQhtr/K5ReiqxSavDAHuNQehg8Nf6QGnPHLlk9J9JRO80C4g6q50WaJUtCSPhPOzvZLpH9k4Fgy7ogOITcEqu2gy+Zncd+sFahKnEff9dQ4J1aQj/ogA+ZY4X+fmg8aIjVC+7RAdeCFvIJ03iSM4JTGrjl9IClWfZS359gd146BW3GF4XeVZ2Tf2AhHgPXBwE7uMIXBwVs5NcYoX9AR8vzOxfV5btK9iSKqnCNQp13F82nsP6rwvsLQJ06/RWVF1KaVo/DDRKwqOFTqKqd ➜ ~
If the host key fingerprint for a server has changed, and you are sure that the new fingerprint is authentic, you can remove old entries with the command (after that you can check the removal using again the find flag -F:
$ ssh-keygen -R 192.168.1.32
➜ ~ ssh-keygen -R 192.168.1.32 # Host 192.168.1.32 found: line 4 /Users/zp/.ssh/known_hosts updated. Original contents retained as /Users/zp/.ssh/known_hosts.old ➜ ~ ➜ ~ ssh-keygen -F 192.168.1.32 -l ➜ ~
Finally, you have to add the response to the bottom of your ~/.ssh/known_hosts file. Either manually, or much easier via:
$ ssh-keyscan -t rsa 192.168.1.32 >> ~/.ssh/known_hosts
However, if you continue having issues with warnings, perhaps the rsa key obtain is not the correct one, and instead of rsa you should have requested a key with another type of algorithm, e.g. dsa. You better have to remove any existing fingerprint for the specific remote host from your known.hosts file and then leave the remote system to return the correct one when you try to connect. So, first, remove any existing fingerprint from your known.hosts file:
$ ssh-keyscan -R 192.168.1.32 $ ssh-keyscan -F 192.168.1.32
Then, try to connect without any key inside the ~/.ssh/known_hosts file. You will receive a warning message ‘Are you sure you want to continue connecting’, but you can proceed by typing ‘yes’. This is exactly the same procedure you follow when you try to connect to your remote system for the very first time (Find info here).
That’s it!
Thank you for reading!